Denial Of Service Attacks
This is when your business, personal website or IT system has come under some form of cyber-attack. Users are then unable to access the systems.
If you believe that you have been the victim of a Cybercrime, you can report it to Police Scotland.
NCSC have guidance to help organisations understand and reduce DoS attacks.
What Are The Two Main Defenses Against Ransomware
In addition to reducing your attack surface, a layered approach to security using antivirus software, firewalls, and multi-factor authentication is also an effective defense strategy that ransomware can thwart.
What is ransomware and how can it be prevented?
Ransomware attackers have ways to bypass cybersecurity measures, but they can protect your business. Tactics to reduce the risk of infection include backups, user training, quarantining suspicious emails, and content filtering.
What are the two main types of ransomware?
While there are innumerable types of ransomware, they mainly fall into two main types of ransomware. These are crypto ransomware and locker ransomware.
What Is Police Ransomware
Police is a malicious program classified as ransomware. This malware is designed to encrypt data and demand payment for decryption. During the encryption process, all affected files are appended with the “.Police” extension. For example, a file originally named something like “1.jpg” would appear as “1.jpg.Police” following encryption.
Once this process is complete, ransom messages are created in a pop-up window and “HOW TO DECRYPT FILES.txt” text files, which are dropped into compromised folders.
The ransom-demand message in the pop-up window and “HOW TO DECRYPT FILES.txt” files is identical. It informs victims that their files have been encrypted. To restore their data, they are to purchase decryption tools from the cyber criminals behind the infection.
The cost of the recovery tools is stated to be US$500 , however, if contact with the criminals is established within the first 72 hours, this can be halved to US$250. Communication is to be initiated via email. Users are warned that they have 70 attempts to enter the correct decryption code.
Should the number of attempts be exceeded, the files will be irreversibly damaged. Unfortunately, in most cases of ransomware infections, decryption is impossible without involvement of the cyber criminals responsible, unless the malware is still in development and/or has significant flaws.
Screenshot of a message encouraging users to pay a ransom to decrypt their compromised data:
Recommended Reading: How To Get A Certified Police Report
Attacks On A Computer System
An attack on a computer system is any type of offensive act that targets computer data, information, infrastructure, network, cloud or any personal computer devices.
A computer attack can range from installing malware on a personal computer to crippling countries’ critical national infrastructure and can be conducted intentionally or recklessly and without authorisation, resulting in damaging, deleting, modifying, or otherwise interfering with or impairing any data or software in any computer system.
Below are some common types of cyber security attacks against computer systems:
- SQL Injection attacks
- Denial-of-Service attacks
- Brute-Force and Dictionary attacks
Cisa Plays Two Key Roles

We Are the Operational Lead for Federal Cybersecurity, or the Federal “dot gov”
CISA acts as the quarterback for the federal cybersecurity team, protecting and defending the home frontour federal civilian government networksin close partnership with the Office of Management and Budget, which is responsible federal cyber security overall. CISA also coordinates the execution of our national cyber defense, leading asset response for significant cyber incidents and ensures that timely and actionable information is shared across federal and non-federal and private sector partners.
We Are the National Coordinator for Critical Infrastructure Security and Resilience
We look at the entire threat picture and work with partners across government and industry to defend against todays threats while securing the nations critical infrastructure against threats that are just over the horizon.
Designed for Collaboration and Partnership
Established in 2018, CISA was created to work across public and private sectors, challenging traditional ways of doing business by engaging with government, industry, academic, and international partners. As threats continue to evolve, we know that no single organization or entity has all the answers for how to address cyber and physical threats to critical infrastructure. By bringing together our insight and capabilities, we can build a collective defense against the threats we face.
Don’t Miss: How To Pull A Police Report Online
Is It Ethical To Pay Ransomware Demands
In the United States, paying the ransom is legal for now, but cybersecurity professionals advise business owners not to do so. According to the value of the assets, an organization may decide it must pay the ransom and that doing so is legal.
FBI agents have a greater understanding of the idea that businesses shouldn’t pay ransom money. They say doing so only exacerbates the problem.
In some situations, it might be in a company’s best interest to pay the ransom. But experts recommend telling the feds or the National Cybersecurity Agency. You can also report it to the Infrastructure Security Agency instead.
What Do Public Agencies Like Fdic Or Uk Gchq Generally Mandate Organizations To Report After Becoming Aware Of A Breach
Data breach notification laws vary based on location and industry. In the United States, the Federal Deposit Insurance Corporation requires banks to report an incident that has or is likely to affect the banks operations, services, or the financial sector no more than 36 hours after they have determined the breach occurred. They are also required to notify their customers as soon as possible if the breach will affect those customers for more than four hours. All banks must comply with these new data breach notification requirements by May 1, 2022.
Reporting in the United Kingdom is governed under the UK General Data Protection Regulation . Under the UK GDPR, all organizations must report a data breach within 72 hours of determining a breach has occurred. Also within the United Kingdom, the National Cyber Security Centre provides advice and support to organizations on how to address cybersecurity threats both through data security and data protection measures to mitigate malware and ransomware attacks.
You May Like: Do You Get Paid For Police Training
Ransomware May Steal Your Data
I have mentioned that a lot of victims are underestimating the possible hazard, thinking that they can deal with the problem without help from authorities. Ransomware developers likely decided to put these self-confident characters down and started to distribute ransomware together with spyware.
Spyware is a type of virus that steals different sorts of data from your computer. Passwords, logins, banking app credentials, personal information, private conversations, corporate documents that are about to be kept away even from the personnel of this company all these things are not private anymore. The first case when a ransomware attack was combined with a data leak happened a year ago, in January 2020. Maze ransomware developers asked for a separate ransom to be paid to delete the information they stole. Later, the private information of the victims that ignored this offer was published on the website in darknet2. Do you still think that it is a good idea to deal with this problem independently?
Private data of Xerox Corporation was published in the darknet after Maze ransomware attack
What Are The Motivations Behind Ransomware Attacks
Cybercriminals Are More Motivated This unequal distribution reflects the two main motivations behind ransomware: politics and money. Increasing international tensions have led to more politically motivated attacks, as evidenced by the rapid trend in government-targeted attacks.
Where do most ransomware attacks come from?
Ransomware is often spread through phishing emails with malicious attachments or drive-by downloads. Drive-by downloads occur when a user unknowingly visits an infected website and then malware is downloaded and installed without the users knowledge.
Who was behind the Kaseya attack?
Who is responsible? The cyberattack was attributed to the ransomware group REvil / Sodinikibi, which held responsible on its dark web leak site Happy Blog. In an update over the weekend, the operators allegedly linked to Russia claimed to have infected more than one million systems.
Who created ransomware virus?
Popp . It was called the AIDS Trojan, also known as the PC cyborg. Popp sent 20,000 infected disks labeled AIDS Information Introductory Diskettes to participants at the World Health Organizations international AIDS conference in Stockholm.
Recommended Reading: What Do Police Drones Look Like
If You Have Been A Victim Of A Ransomware Attack Such As This Our Advice Is:
- You should restart your PC. This has been known to delete the message.
- Action Fraud strongly recommend that anti-virus software is both used and routinely updated to keep pace with new threats as they are discovered. In addition, operating systems such as Windows and Mac OS routinely issue updates that patch potential vulnerabilities.
- Report the ransomware attack to Action Fraud.
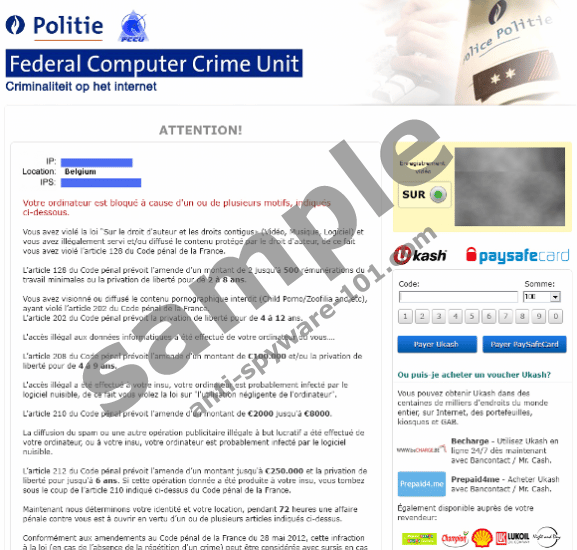
- To protect against fraud in the future, never reveal Ukash vouchers or voucher codes, or Paysafecard PINs by e-mail or over the telephone, and it is advised that vouchers or PINs are only used at participating Ukash or Paysafecard merchants.
To report a fraud, call Action Fraud on 0300 123 2040 or use our online fraud reporting tool.
Ransomware Victims Aren’t Reporting Attacks To Police That’s Causing A Big Problem
Many victims of ransomware aren’t reporting attacks to police, making it harder to measure the level of crime and to tackle the gangs involved.
Europol’sInternet Organised Crime Threat Assessment 2020 report details the key forms of cybercrime that pose a threat to businesses right now and ransomware remains one of the main concerns, especially as these gangs increasingly display high levels of skill and sophistication.
You May Like: How To Be A Police Officer In Oregon
Can Ransomware Spread Through Vpn
A VPN cant stop ransomware, but it can make you less vulnerable to attack. A VPN hides your IP address and encrypts your traffic and data, making it harder for ransomware creators to attack you. This may interest you : What is a famous ransomware attack?. your stored files or your computer system are not encrypted so hackers can still access them to hold you for ransom.
How many types of ransomware are there?
Two types of ransomware in particular are very popular:
- Locker ransomware. This type of malware blocks basic computer functions.
- Crypto ransomware. The goal of crypto ransomware is to encrypt your important data such as documents, pictures and videos, but not to interfere with basic computer functions.
Can ransomware spread through network?
Ransomware usually spreads through spam, phishing emails, or through social engineering efforts. It can also be spread through websites or drive-by downloads to infect an endpoint and break into the network. once the ransomware is installed, it locks any files it can access with strong encryption.
How long does ransomware take to encrypt files?
In-depth and careful research has shown that the average time it takes ransomware to start encrypting the files on your PC or network is only 3 seconds.
Can You Report Ransomware To The Police
If you are a victim of ransomware: Contact your local FBI office for assistance, or send a suggestion online. On the same subject : What are some famous malware attacks?. Report to the FBIs Internet Crime Complaint Center .
Should I report a ransomware attack?
If in doubt, Report It Out. Victims of ransomware should report to federal law enforcement via IC3 or a Secret Service Office, and may request technical assistance or provide information to assist others by contacting CISA.
Recommended Reading: What Degrees Are Good For Police Officers
Reporting Ransomware Attacks Is Only The First Step
Once a company has reported a ransomware attack and recovered, its focus needs to turn toward ransomware prevention. Mellen said a company’s first steps should include performing security monitoring and having a business continuity plan and ransomware incident response plan in place, as well as a team ready to execute on those plans.
Once your company recovers from the attack, tips for enterprise ransomware prevention include having strong email protections and controls, implementing multifactor authentication and using role-based access control. Another important aspect is ensuring a strong security awareness program is in place to educate employees about how bad actors attempt to get their malicious software onto the corporate network, especially via social engineering.
Next Steps
Why We Need Your Help
New ransomware variants are emerging regularly. Cyber security companies reported that in the first several months of 2016, global ransomware infections were at an all-time high. Within the first weeks of its release, one particular ransomware variant compromised an estimated 100,000 computers a day.
Ransomware infections impact individual users and businesses regardless of size or industry by causing service disruptions, financial loss, and in some cases, permanent loss of valuable data. While ransomware infection statistics are often highlighted in the media and by computer security companies, it has been challenging for the FBI to ascertain the true number of ransomware victims as many infections go unreported to law enforcement.
Victims may not report to law enforcement for a number of reasons, including concerns over not knowing where and to whom to report not feeling their loss warrants law enforcement attention concerns over privacy, business reputation, or regulatory data breach reporting requirements or embarrassment. Additionally, those who resolve the issue internally either by paying the ransom or by restoring their files from back-ups may not feel a need to contact law enforcement.
Don’t Miss: Can You Request A Police Report
Identify The Ransomware Infection:
To properly handle an infection, one must first identify it. Some ransomware infections use ransom-demand messages as an introduction .
This, however, is rare. In most cases, ransomware infections deliver more direct messages simply stating that data is encrypted and that victims must pay some sort of ransom. Note that ransomware-type infections typically generate messages with different file names . Therefore, using the name of a ransom message may seem like a good way to identify the infection. The problem is that most of these names are generic and some infections use the same names, even though the delivered messages are different and the infections themselves are unrelated. Therefore, using the message filename alone can be ineffective and even lead to permanent data loss .
Another way to identify a ransomware infection is to check the file extension, which is appended to each encrypted file. Ransomware infections are often named by the extensions they append .
This method is only effective, however, when the appended extension is unique – many ransomware infections append a generic extension . In these cases, identifying ransomware by its appended extension becomes impossible.
One of the easiest and quickest ways to identify a ransomware infection is to use the ID Ransomware website. This service supports most existing ransomware infections. Victims simply upload a ransom message and/or one encrypted file .
Example 1 :
Example 2 :
Can Malwarebytes Remove Ransomware
Malwarebytes can detect and remove ransomware without further user interaction.
Does AVG remove ransomware?
AVG AntiVirus FREE is a top-notch ransomware scanning and removal tool. It is a comprehensive security solution to protect against ransomware attacks as well as many other types of malware and online threats.
Does Malwarebytes stop ransomware?
It actively prevents aggressive ransomware from taking over your devices and demanding payments in order to preserve your files. Malwarebytes Premium even fights against threats that traditional antivirus cannot stop, and blocks zero-day ransomware attacks .
Can Avast remove ransomware?
Avast Free Antivirus can detect and delete many types of ransomware quickly and easily. It will also help keep your Windows PC safe from all kinds of cyber attacks in the future.
Also Check: How To Become A Police Officer
How Reporting A Ransomware Attack Helps Your Business
While reporting a ransomware attack can eventually lead to the indictment and prosecution of cyber criminals across the world, you may be wondering, how can reporting a ransomware attack help my organization today?
The U.S. Cybersecurity and Infrastructure Security Agency publishes alerts and bulletins through the National Cyber Awareness System that specifically shows how ransomware and other malware variants work.
By reporting a ransomware attack, you contribute to the data used to create advisories and alerts that provide your organization and others with critical information on security issues, vulnerabilities, and active cyber crimes. The data in these publicly available alerts are compiled through reports submitted by ransomware victims.
Its even possible a government agency might have a without having to contact the threat actor. Youll never know unless you reach out and report the incident!
Unfortunately, due to the volume of reports filed and the limited government resources available, reporting a ransomware attack does not typically lead to answers for your organizations specific incident.
However, law enforcement can provide advice to remediate the damage that occurred to your network and connect you with the ransomware recovery resources that may be able to help you with the recovery process.
Should I Report A Ransomware Attack
The short answer is yes. However, we recognize that the decision to report a ransomware attack to law enforcement can feel too complex to be covered by a simple yes or no answer.
To address your concerns about filing a report, weve answered the common questions our clients ask when considering reporting a ransomware attack below:
Don’t Miss: What Kind Of Body Armor Do Police Wear
Warning Signs And How To Protect Yourself
- Be cautious of any unsolicited email
- Do not respond to suspicious emails and do not click on any links in them
- Ensure a backup plan for your data that is consistent and frequent
- Have multi-factor authentication and anti-malware software
- Ensure regular software and system updates/patches as well as frequent system-wide password changes
- Publish and enforce an employee security policy
- Work with law enforcement when developing and testing an incident response plan
- Report, report, report!
- Visit the Canadian Centre for Cyber Security for additional information on ransomware and cyber security advice, guidance and services
Is Ransomware A Crime

Ransomware is illegal because it charges a ransom fee in addition to collecting your information on the computer. The added burden on the victim is that they will be asked to pay in bitcoins. This is how cyber criminals hide from the authorities.
Is ransomware a criminal?
First, federal criminal laws like the Computer Fraud and Abuse Act can be used to prosecute those who perpetrate ransomware attacks. Other cyber precaution laws authorize federal authorities to support private companies operating in critical infrastructure sectors in securing their systems.
Is using ransomware illegal?
However, it turns out that paying the ransom money from a ransomware attack could be illegal. Thats right, in a 2020 ruling, the Treasury Departments Office of Foreign Assets Control and the Financial Crimes Enforcement Network made it illegal to pay ransom in some cases.
Recommended Reading: Can I Report Online Harassment To The Police