How Do You Find Out Who Is Behind A Textnow Number
According to TextNow support, you cant track who owns TextNow number as they do not reveal information about the identity of a person who is using a particular number. If you plan to reach out to their support team, that wouldnt be much of a help to you. You may try visiting the profile which you want to track.
Annoying Or Obscene Telephone Calls
Massachusetts General Law Ch. 269 Sec. 14a
Annoying, harassing, hang-up, or obscene telephone calls are becoming more and more commonplace today even with advanced technology in communications, such as Caller ID and dialing *69. Today, were able to trace a phone call back to the caller by pressing a couple of buttons on your telephone. This is an excellent tool for the homeowner and law enforcement to identify the caller.
These types of calls are evident in bad relationships, the breakup of a relationship, a disgruntled employee, unhappy customer, a neighbor and the like. The caller has a sole purpose to annoy or harass. There is a solution and these types of calls can be stopped.
In Massachusetts, MA General Law c. 269 s. 14A is the chapter and section that one can be charged with for annoying or obscene telephone calls. There are 3 elements to the law that must be met. The person repeatedly made telephone calls or caused telephone calls to be made , to the victim or the victims family and the persons language was indecent or obscene, or the persons sole purpose was to harass or molest the victim or the victims family. Penalty: Misdemeanor.
Some Initial Steps To Take
Some people cannot afford to change their phone number and their only action is to trace the calls.
Tracing Phone Calls
When you want to trace a phone call:
How Do I Find Out Whos Making the Phone Calls?
If You Are Concerned About Your Cell Phone Being Tracked By The Police Call Our Experienced Criminal Defense Attorneys Today
Tracking your cell phones location, except in the cases of extreme, exigent circumstances, requires the police to obtain a warrant. However, it is often the case that police officers will ignore this requirement and simply hope that you do not know the law and do not have a competent attorney to challenge their authority. This is why it is vital to retain a skilled Utah criminal defense attorney like those at Overson Law, PLLC if you believe you have been the subject of an illegal search, including illegal tracking of your movements. We will work to suppress any evidence obtained outside of the proper channels. Call our firm today at 758-2287 for a free consultation.
Don’t Miss: How Do You Get A Police Report Online
Can The Police Track My Phone Even If I Remove The Sim Card
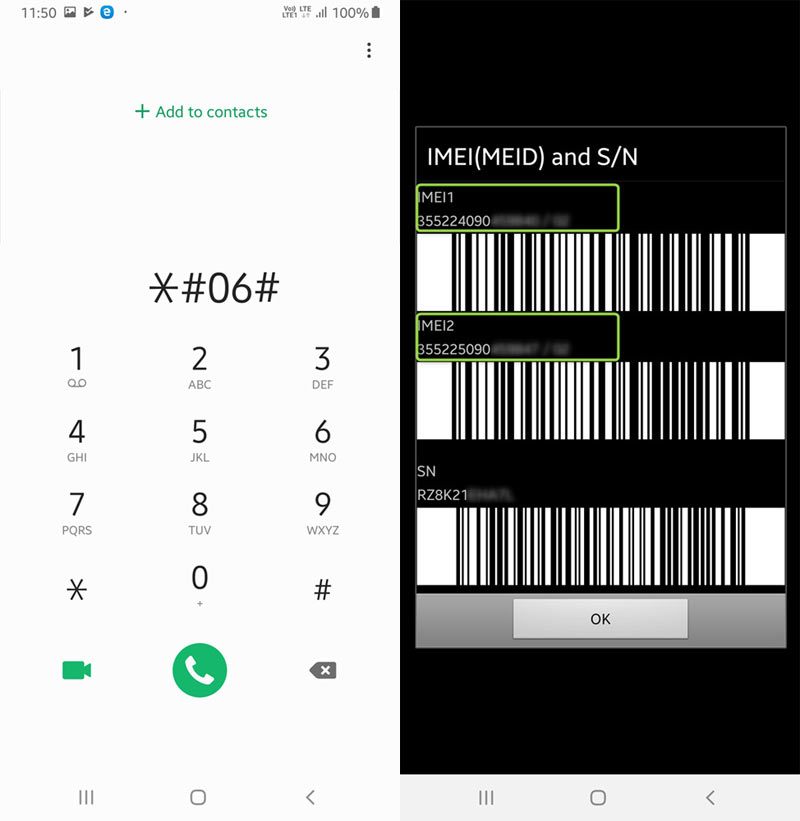
If the Police have your mobile phone number then I understand they can track your mobile phone. Now, I understand the mobile phone number is linked to the sim card but if you simply change the sim card does that stop the Police from tracking you? Because I also understand that all mobile phones have a IMEI number.
Can the fact they had the sim card mobile number while inserted into a mobile phone give them access to that number so even if you change the sim card, they can track the mobile phone no matter what sim card is inserted? Hence, if so, is a new mobile phone and sim card is the only option ?
It depends on the method you are being tracked. If we are talking about a wiretap, then the tracking is being done at the telco and as long as you maintain the same phone number, regardless of SIM or phone, it will get captured. If we are talking about false mobile towers, like Stingray devices, then you are being tracked by multiple factors SIM, phone number, IMEI, etc.
I dont know the technical details to answer your specific question, but it might not be relevant.
Abandon Sms And Switch To Encrypted Messaging Apps
The simplest and best way to protect against SIM cloning attacks, as well as eavesdropping by stingrays, controversial phone surveillance devices that law enforcement has a history of using against protesters, is to stop using SMS and normal phone calls as much as possible. These are not and have never been secure.
Instead, you can avoid most communication surveillance by using an end-to-end encrypted messaging app. The Signal app is a great choice. Its easy to use and designed to hold as little information about its users as possible. It also lets Android users securely talk with their iPhone compatriots. You can use it for secure text messages, texting groups, and voice and video calls. Heres a detailed guide to securing Signal.
Signal requires sharing your phone number with others to use it. If youd rather use usernames instead of phone numbers, Wire and Keybase are both good options.
Read Also: What Handcuffs Do Police Use
Also Check: How To Apply In Police Academy
Mpds $15000 Graykey Iphone Unlocking Tool
The documents obtained by Wisconsin Examiner also show MPD purchaseda GrayKey iPhone unlocking tool in Sept. 2018. The actual device came in at $15,000, along with an $18,000 contract for licenses. In Oct. 2019, the city renewed its licenses for GrayKey, purchasing three licenses for $54,000.
GrayKey is produced by the American company Grayshift, and is used to break into passcode-protected iPhones. Unlike a CSS, which traces phones from a distance, GrayKey needs to be physically plugged into the phone. This often occurs when phones are taken by police as part of an ongoing investigation.
The cell tower simulator and the cellphone unlocking tool access different forms of phone information, and in different ways. Theyre not both accessing cell data, noted Katz-Lacabe. One of them, a , is basically tracking down the radio communication between your phone and a cell site tower. So that communication means your voice traveling over that, potentially, and your text messages. But its not intercepting, say, your web traffic. Or your traffic from encrypted communication or web browsing. That stuff is still protected by other layers of encryption.
How To Catch A Spoof Caller
Tracing a spoofed phone number and catching a spoofed caller is not easy. Definitely not as easy as identifying an anonymous Twitter user, the sender of an anonymous email or the person behind internet posting and blogging. Some spoofing services allow the anonymous caller or text message sender to receive replies. In such cases, Rexxfield investigators can often trace a number by tracing the spoof text messages and positively identify the individual responsible for the spoofing harassment. Even out-of-court. These cases are mostly harassment cases. Because the cyberbully wants to hurt someone, they want to engage in a conversation. This allows you to send and receive text messages. By tracing anonymous text messages, we can trace a number and catch a spoof caller.
However, most spoofing services are one way only, especially when it comes to scams. The person can send messages to you, but you cannot reply. In these one-way cases, it may not be possible to identify the origins of the spoofed messages or calls. Except through criminal or civil court proceedings which leverage the use of subpoena or warrants to obtain forensic evidence that may ultimately lead to uncloaking the antagonist.
You May Like: How To Get My Police Record Online
Where To Get Further Help
If you are a suspect or a witness in a criminal case, and the police are seeking to extract data from your phone, make sure you know your rights. As a defendant, you are entitled to legal representation in your case. Your criminal defence solicitor can explain the rules surrounding disclosure and advise you on your options. Instructing a solicitor who understands the nuances of the system could make all the difference. Contact Stuart Miller Solicitors for a free no-obligation consultation today.
Spyic The Hidden Ninja App That Keeps An Eye On The Target 247
You might never have heard of Spyic before. However, today you are going to be glad that you found out about Spyic from me.
Spyic is a phone monitoring app that is used by millions of people all over the world. It has a lot of features that provide you with every bit of data on the target phone constantly.
It is a web-based service that constantly keeps a watch on the target user and his cellphone activity. Not only you will know where the person is, but Spyic will also give you so many other valuable data.
If you want to monitor your child, Spyic will let you know if your kid is safe from online predators and other negative elements of society. If you want to monitor your significant other, Spyic will reveal to you if they are cheating for you.
And the best part? You dont have to root or jailbreak the target device in order for Spyic to monitor it. This is a very unique feature and I didnt find it in any of its competitors.
Spyic is more or less like your best friend in any scenario. Here is an idea of what it has to offer.
Also Check: How To Obtain A Copy Of A Police Report
Tracing A Threatening Or Harassing Phone Call
A security feature has been installed on most UT phone lines that will capture Caller ID information even if a caller has blocked that information. The feature increases the security of all UT faculty, staff and dormitory residents by helping law enforcement officials locate the origin of threatening or harassing phone calls. This feature should only be used to identify a phone number if the call is threatening or harassing. Using Call Trace should be considered the same as filing a complaint with UTPD.
Can I Get An Old Phone Number Back
You might be able to get back your old phone number. Changing phone numbers is inconvenient and, at times, unnecessary. Maintaining the same phone number while changing phone plans or carriers is entirely possible.The carrier maintains the number, however, and you can inquire about reinstating your old number.
Recommended Reading: How To Become A Capitol Police Officer
What Are Second Text Apps All About
To learn how to trace a texting app number, you need to know some basics. If you look upon the Play/App Store, then you can find tons of second text apps. Some of these popular text apps are as follows:
Most of these apps would ideally work in the same way. While setting up your account, you can link your app with a second virtual number. The virtual number can be from any other country that would be simply linked to the app. Once you have the virtual number, you can use the app to text anyone and your original number will not be displayed.
What Is A Stingray

Stingray is the generic name for an electronic surveillance tool that simulates a cell phone tower in order to force mobile phones and other devices to connect to it instead of to a legitimate cell tower. In doing so, the phone or other device reveals information about itself and its user to the operator of the stingray. Other common names for the tool are cell-site simulator and IMSI catcher.
You May Like: How To Report A Stalker To Police
Can The Police Hack Your Phone If It Is Seized In A Search
Where the police seize your mobile phone, they will often be able to use technology to extract its contents without you giving them your pin code. Whether this is possible depends on the type of phone that you have. New iPhones are difficult to hack, whereas older iPhones and Android phones are easier for the police to access. Mobile phones with SSD hard drives are more difficult for the police to hack because they regularly strip themselves of deleted data. Sometimes, the police outsource mobile phone extraction to private companies that then provide the extracted data to the police.
The Information Commissioners Office has raised concerns that police forces are over-zealous in their approach to mobile phone extraction, leading to a situation where data is extracted unnecessarily. This impacts not only upon suspects, but also upon victims and witnesses. The ICO called for tighter regulation of mobile phone extraction.
I Should Be Charging For All My Info
From Bob on March 19, 2021 :: 4:36 am
what you normal regular people need to understand is this. Stop being so damn gullible. Dont open everything you receive. NEVER absolutely NEVER open a text or email from someone you dont know just by opening it you grant access from even the dumbest hackers. And you dont just factory reset a device and it be all good. Factory reset doesnt delete EVERYTHING first you have to delete and wipe your cache logs ALL OF THEM then factory reset. I am a hacker. You delete the cache logs because every password ever used on that phone honestly everything ever done with that phone can be seen or retrieved from your cache logs EVERYTHING. I tell you this because Im sick of all these wannabe no degree dipshit 3rd world country faggots trying to get 1 over on the U.S. theyre lame and skills suck. Keep on comin at me Imnotthe1 and above all use a damn VPN pay for it its worth it or if your info means that little to you get the mayivpn its free and works pretty good. And turn off you Gdamn nfc payment its the devils gateway for the lamest dipshit to steal your info and not even the best hacker would know if it happened if their nfc was on. Developer mode bluetooth debugging run off built nfc stripper app
You May Like: How To Obtain A Police Report In Pa
How Can I Find Someones Location Using Their Cell Phone Number
To get real-time results, IMEI & GPS call trackers can be used to track the location of a phone call. Apps like GPS Phone & Locate Any Phone are great with tracking mobile phones, even when the phone is not connected to the internet. You can know the GPS coordinates of a phone number within seconds.
Dont Miss: How To Hire A Police Officer For A Party
Cellphone And Smart Device Location Data: Where Does It Come From
Cellphone and wireless service providers and tech companies store certain historical and real-time location data gleaned from cellphone connections with cell towers, GPS satellite tracking, and smart device applications and operating systems. Law enforcement can request this data using a court order or warrant. Some examples of this data include:
Historical CSLI. A typical cellphone produces a time-stamped record every time it connects to a cell site. This record is referred to as “cell-site location information” . With CSLI, police can get a really good idea of where someone’s phone has been, allowing them to piece together past eventsfor instance, connecting the dots as to a suspect’s location at the scene of a crime.
Real-time CSLI. To obtain real-time data, a service provider can either contemporaneously monitor a phone’s CSLI connections or “ping” a user’s cellphone and force it to reveal its location. This real-time data can provides police with information on a suspect’s current whereabouts.
GPS movements. A phone or car’s GPS system tracks its movements using satellite signals. This information might be stored on the phone or vehicle itself or transmitted to a repository. It can also be relayed to police in real time.
Recommended Reading: How To Put An Anonymous Tip Into The Police
Can Police Force Me To Give Up My Cellphone Password
Generally, the only place where law enforcement can force you to give up a cellphone password is at a border crossing. Border officers are given powers to screen people and goods entering the country under the Customs Act. A cellphone is considered good being brought into the country, and so are the contents inside.
In one case, a man argued his rights had been breached after Canada Border Services Agency officers took him to secondary inspection and required him to provide his passwords for his computer and phone. However, it has long been established that there is a reduced expectation of privacy at border crossings.
Heres what the judge said:
While it is undeniable that a cell phone and a personal computer can contain large amounts of personal and private information, it is also true that people choose to seek entry into Canada and Canada, through its Border Services officers, is entitled to screen who it allows into the country on the basis of the goods they are seeking to bring with them, among other requirements.
I do not find that, in this context, the requirement to provide a password offends the right to be free from self-incrimination. To hold otherwise would have the result of an enhanced right against self-incrimination at the border.
How Do I Find My Friend Lost Phone
Remotely find, lock, or erase
Recommended Reading: How To Make Police Report For Identity Theft
Also Check: How To Get Accident Report From Police
Limits To The Cellphone Search Rule
Prosecutors expressed a series of objections to the requirement that officers obtain warrants before searching arrestees cellphones. They mentioned remote wiping, by which a third party could delete a phones data after police officers take it, or by which the data might erase if the phone enters or exits a particular geographic area. They also discussed data encryption, which makes information nearly impossible to get to without a password. They even invoked extreme scenarios, as where a phone has the location of an about-to-explode bomb or a missing child.
First, to the extent that a cellphone might be usable as a weapon, the Supreme Court said that officers can search it without a warrantfor example, they can retrieve a razor blade hidden between the phone and its case. Second, officers can probably take preventive measures to avoid the loss of a phones data. Without delving into it, they could turn off the phone, place it in a bag that protects against radio waves, or disable its automatic encryption lock, for example. Third, with todays technology, it may take officers as little as 15 minutes to get a warrant that authorizes a search. And fourth, officers can dig into the phone when theres an emergency.